NoName057 Strikes Again

25 Nov 25

After several weeks of inactivity in Spain, the pro-Russian hacktivist group NoName057 has re-emerged. Following the announcement of new support measures for Ukraine by our government last week, we immediately anticipated that a reprisal of this nature could occur.
As expected, managing over 10,000 websites—many of which belong to Public Administrations—it is inevitable that we would be among this group’s targets. The truth is, they have evolved their modus operandi over time. They have shifted from relatively simple Denial-of-Service (DoS) attacks with significant volume to slightly more sophisticated assaults, combining various methods, User-Agents, URIs, and payloads.
The Transparent Edge team constantly strives to stay ahead of the latest attacks. While these attacks do not pose a threat to the stability of our platform, they are a risk to many of our clients. Their current techniques focus on lower volume but are more evasive, designed to bypass security measures and intermediate layers such as CDNs.
The traffic is highly distributed, originating from multiple countries (39), over 35 Autonomous System Numbers (ASNs), and a total of 43 unique User-Agents detected by us to date. This data does not imply that they can only attack from foreign countries or ASNs; rather, it represents the information we have gathered to understand their new attack pattern.
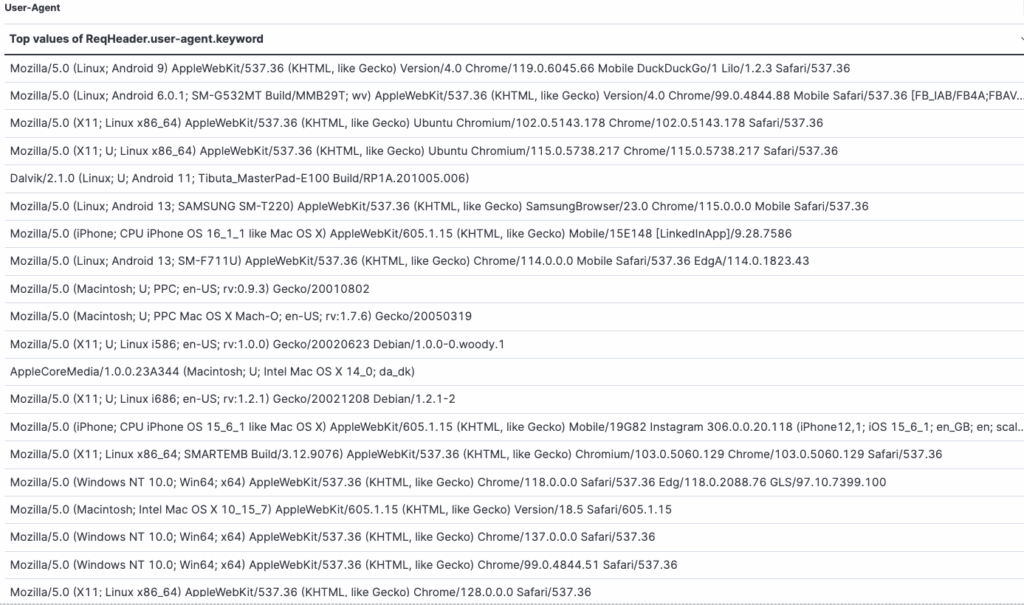
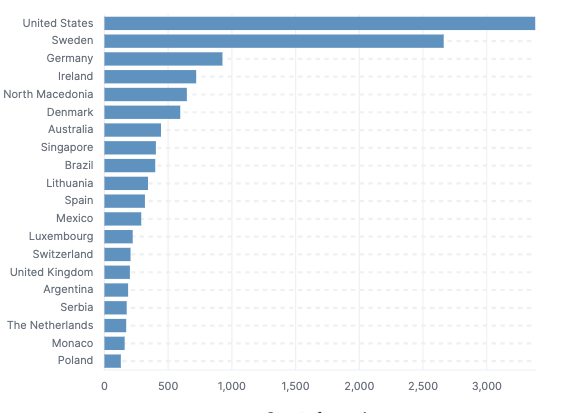
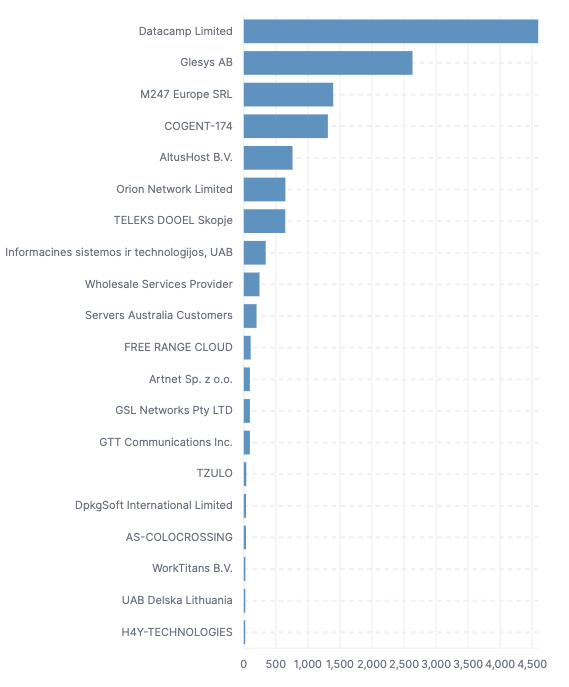
The information gathered is interesting from the perspective of learning more about their modus operandi. However, as stated, there are no guarantees that they will only use these specific ASNs or countries, as this network is based on a botnet where anyone can install their software and dedicate their computer to the cause.
Nevertheless, a thorough examination of their attack vector allows us to create a pattern profile based on certain characteristics, making their attacks easily identifiable. By utilizing a statistical isolation system, we have successfully discriminated the requests arriving at our systems into two categories: legitimate requests and NoName requests. This ‘fingerprinting’ capability allows us to mitigate their attacks much faster, preventing them from causing damage to the targeted systems.
Jorge Román is the Co-founder and General Director (CEO) of Transparent Edge.
Jorge Román is a Systems Engineer who, over the years, gave way to the CEO within him, or perhaps a CEO who, over the years, gave way to the Systems Engineer within him. He’s not entirely sure, and he often ponders it while mopping the office floor and serving coffee. The rest of the time, he directs the first Spanish-born CDN, raises two daughters, and still finds time to read about entrepreneurship. As for sleeping, he’s saving that for another lifetime.