Integrating passkeys into the login flow for passwordless authentication

07 Jul 25

One day, an IT guy buys a coffee maker and thinks: “Please, let the coffee maker use passkeys.”
Every day, the news brings with it some reference to password breaches, new database leaks, and multiple security breaches. The situation only seems to be escalating in frequency and complexity.
That’s why the integration of access keys (passkeys) into the login flow represents a true evolution in web authentication. Passkeys eliminate the need for traditional passwords and offer a more secure and convenient alternative for users.
Essentially, registering a passkey involves associating a unique access key with a user’s account on a website or web application, and then securely storing that passkey’s public key on the service provider’s server.
For the user, everything seems instantaneous: touch a button, use your face or fingerprint, and voila! you’re in. Behind that simplicity, there’s much more to it.
To achieve user fluidity, there is a solid and well-defined process that involves key generation and verification, cryptographic validation, and good coordination between the browser, backend, and password provider.
The process of creating a passkey requires a coordinated interaction between four main components:
navigator.credentials.create() function. This opens a system dialog (Face ID, fingerprint, PIN, etc.), and if all goes well, the passkey provider generates the key pair. The private key remains on the device, and the public key (along with other data) is returned to the browser, which in turn sends it to the backend for storage.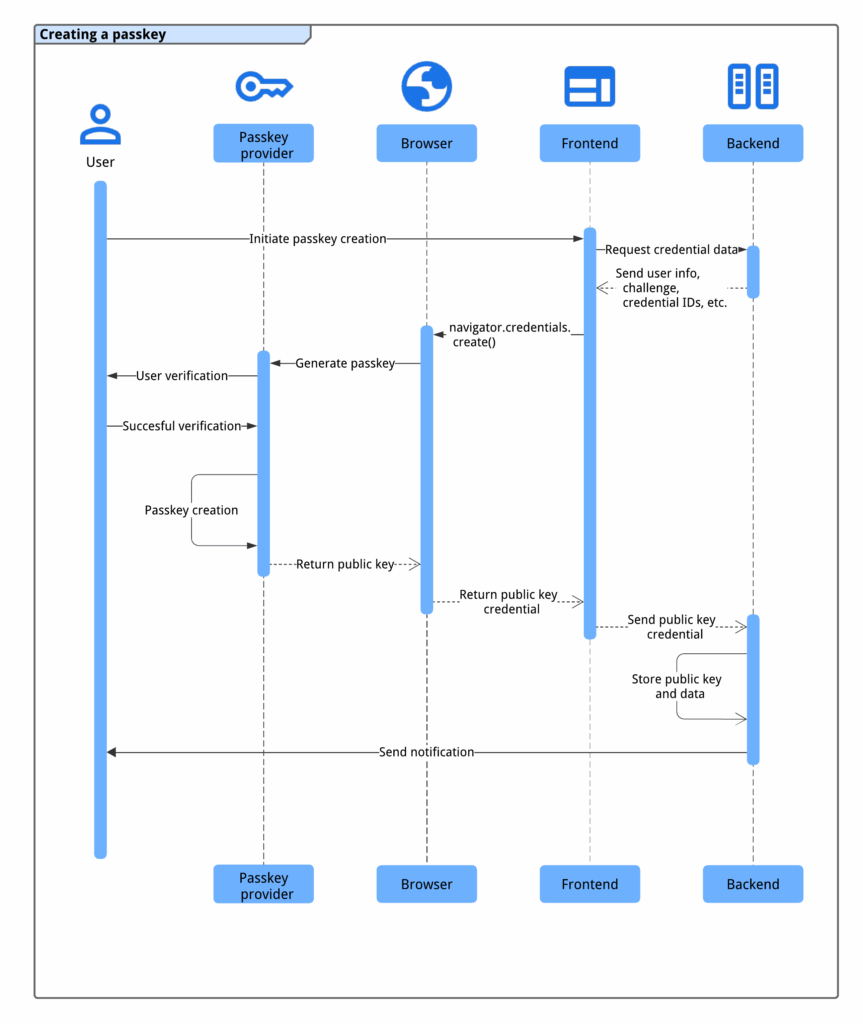
Integrating passkeys is a step forward in access security: it eliminates passwords, improves the user experience, and strengthens resistance to common attacks like phishing.
The result is simplicity, less friction, greater security, and an experience that finally feels like something of our century.
The tech guy sighs “I no longer have to remember my coffee subscription password, the grinder password, the server app password, and the Wi-Fi password. My brain is already full of passwords for routers that no one ever resets! Besides, if the coffee maker doesn’t have an interface, what’s the point of being an IT tech?”
Antonio Bacete is a Frontend Solutions Architect at Transparent Edge.
If Manchego cheese were code, it would have Antonio Bacete’s face on the label. A tireless developer, Antonio is in charge of frontend architecture and development at Transparent Edge, where he patiently molds and integrates every feature we dream up for our dashboard.